So you’ve just unpacked your latest IoT device, a wireless baby monitor. You were skeptical about this new wave of tech, but you can justify this one since what’s the worst that will happen? Some hackers get to see your baby sleeping in an unidentifiable room? So you give it the wi-fi password, download the app, and sure enough, there’s your child sleeping peacefully. The problem is, while your IoT Security might be safe, there’s a lot of problems a vulnerable device can cause.

Despite the numerous startups supporting the idea of smart homes, most consumers aren’t ready for the concept. In fact, based on recent survey data, it would be fair to say that the majority of potential users aren’t quite willing to pay the amounts needed to make an actual Internet of Things living space. It’s an odd stumbling block considering that, from an expert standpoint, the biggest issue with Smart Home technology isn’t the cost, it’s your overall IoT security.
It’s no great surprise that security on a wireless home network is an issue. If a user has so many devices open to a wi-fi signal only one of them needs to be vulnerable for the whole system to be compromised. And, sure enough, there is a variety of malware already out there attempting to access these devices.
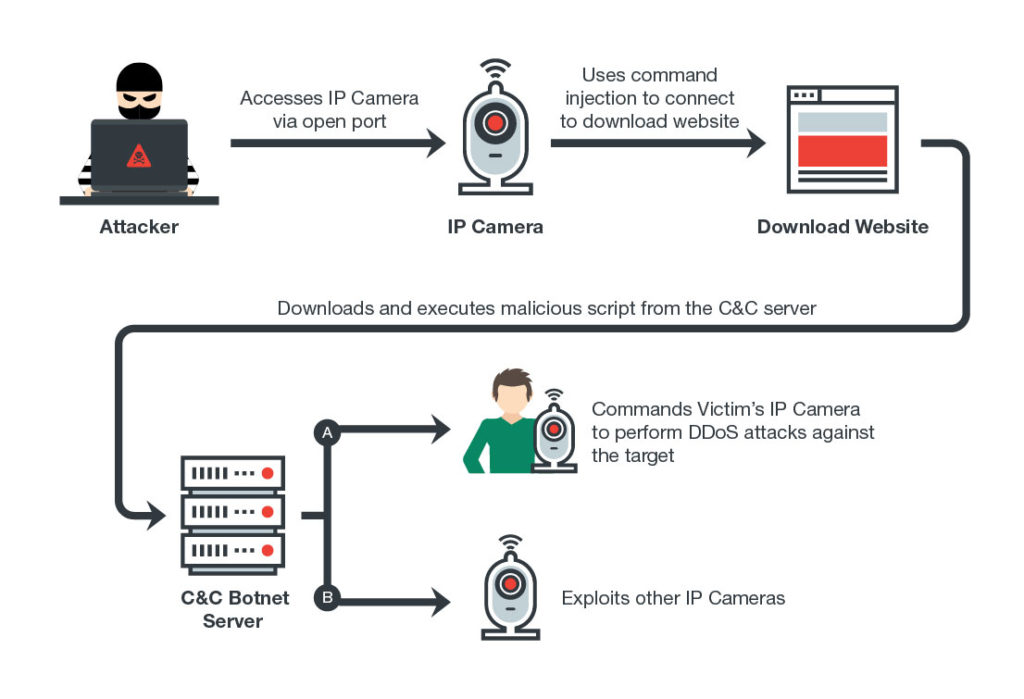
The most recent insurgent is a little devil called Persirai that targets IP cameras on a user’s network. This malware allows the hacker to carry out DDoS attacks on a user’s network by overwhelming it with data from multiple sources. According to cyber security research staff at Trend Micro, that this particular malware is targeting “over 1,000 Internet Protocol (IP) Camera models based on various Original Equipment Manufacturer (OEM) products.”
The problem is the vast majority of users are not aware that their cameras or any of their smart home devices are vulnerable in the first place. In the case of cameras, a quick by Trend Micro search using the IoT search engine Shodan reveals over 120,000 cameras worldwide that are currently vulnerable to Persirai as well as similar malware.

The problem is most of the IoT devices, right out of the box, don’t always contain the best IoT security. This issue was revealed last year with Mirai, which caused the largest internet blackout in US history. It did so by using internet connected devices such as surveillance cameras and other smart home devices and turned them against Dyn, the domain name system provider for hundreds of major websites including Spotify, Twitter, Wired, and Vox. Then, only a month later, a new permutation of Mirai took out nearly a million users in Europe, after finding an exploit in Zyxel (and similar) Internet routers that had an open port for maintenance by IPs.
At this time the only option for most end users to ensure their network is safe and not part of a massive DDoS Botnet is either doing extensive research on the products they purchase to find out how safe they are or to forgo joining the world of IoT altogether. As it is, it seems the biggest concern isn’t the theft of our data but rather how someone uses our devices against someone else.

